USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium

USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium

PDF) Spyduino: Arduino as a HID exploiting the BadUSB vulnerability | Vagelis Karystinos - Academia.edu
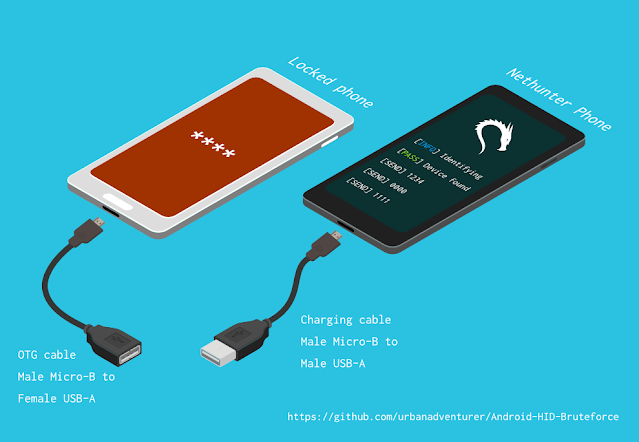
Android-PIN-Bruteforce - Unlock An Android Phone (Or Device) By Bruteforcing The Lockscreen PIN - RedPacket Security